Agilitest allows the recording of variables which are then encrypted in ATS files.
How to manage encrypted passwords
This allows them not to appear in plain text in the files, nor in the test editing interface.
You can access the use of an encrypted password through the shortcut located in the special keys when entering text.
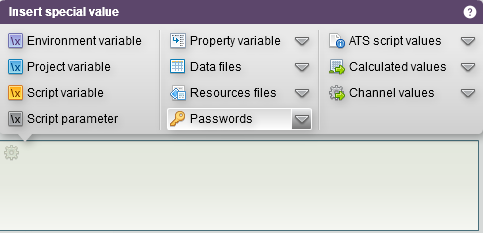
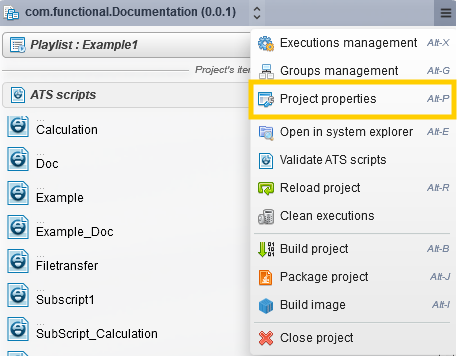
They can also be managed in the "Edit project properties" menu.
Click on "Add" and enter a name and a value.
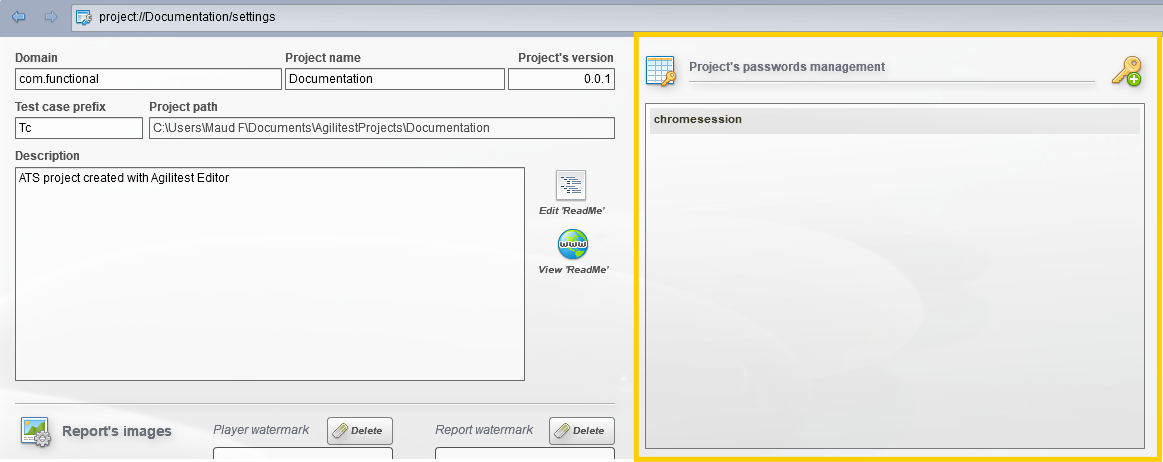
Thereafter, the value can be retrieved in ATS as a normal variable using the keyword $pass(variable).
What differs from the normal management of variables:
- Passwords are not printed in the editor user interface anywhere other than in their edit menu.
- They are not visible in ATS files, not even their declarations.
- They do not appear in ATSV files.
- They do not appear in the logs and logs generated by Agilitest and ATS.
- Each variable declared using $pass() variables is handled in the same way.

When to use encrypted passwords
We recommend that you use encrypted passwords when you cannot do otherwise.
For example, we do not recommend that you perform your tests with real user accounts that are in your teams by encrypting passwords. The solution that we recommend to you is to create users dedicated to tests and having their own privileges, if possible limited.
If you cannot do otherwise, for example if you must test the administrator account, we advise you to do so on environments similar to production that are secured differently (for example physically on your premises).
Finally, if you are testing on systems that are in the cloud, you will not be able to do otherwise, and in this case, we advise you to complete this mechanism, for example by going through secure transfer protocols like https or using one-time passwords issued by a secure server.
Technical functioning of passwords
Passwords are encrypted in Agilitest.
Password encryption with ATS is AES (Advanced Encryption Standard) in CBC mode (Cipher Block Chaining) with PKCS5Padding which is a symmetric encryption algorithm. Therefore, a secret key is used for password encryption.
By default, this secret key (if nothing is done or modified) will have this value: "ats_key_crypto-1"
This use of keys is sufficient in the case of a sufficiently secure corporate environment with users of an ATS testing project.
Each password will be encrypted in its own file, which is located in the directory: src/assets/secret with the atsc extension (example: mypassword.atsc).
The mechanism is designed to enable passwords to be shared between all users of an ATS project, but also in the case of continuous integration execution.
This secret key can modified in two manners:
- By adding this key to the .atsProjectProperties file for each project, placing another secret password encryption key in the “atsKey” property.
- By defining an environment variable called “ATS_KEY” at the operating system level with the value of the secret key used for data encryption.
🔶Warning
When using the environment variable, it is essential to set this environment variable with the correct key on the test designers' machines and on the test execution machines. Otherwise, the data will not be decrypted.


